Cybersecurity
How To Secure Online Banking
Since the invention of the internet, many things have changed, including how we bank and access our accounts. Long ago in the before time, people had to visit a local bank branch to make deposits and withdrawals. However, today people deposit checks by taking a picture of it on their phone. Approximately 73% of people…
Read More6 Tips To Secure Your Cloud Apps
Companies often overlook misconfigurations of cloud solutions when planning cybersecurity strategies. Signing up for cloud apps typically goes quick and easy, leading users to assume that security gets automatically taken care of. However, this assumption is incorrect because cloud security follows a shared model. While the provider secures the backend infrastructure, the responsibility falls on…
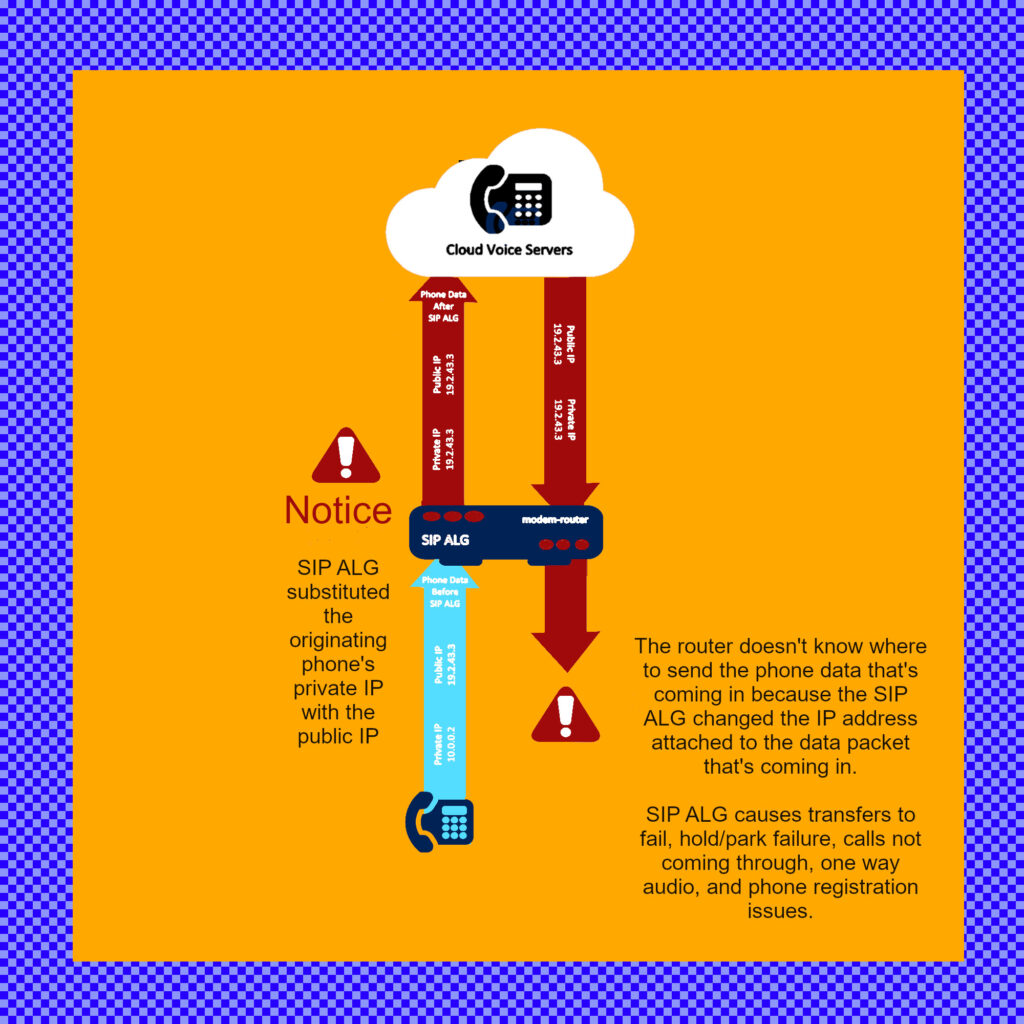
Read MoreSIP ALG: Why Turn It Off
Session Initiation Protocol (SIP) offers a widely used protocol for initiating, maintaining, modifying and terminating real-time multimedia sessions between endpoints on the Internet. SIP became an integral part of the modern communication infrastructure since it’s invention. It gets used in a variety of applications today. Apps include voice and video over IP (VoIP), instant messaging,…
Read MoreIs That Text From Your CEO A Scam?
Imagine working away at your job when you suddenly receive a text from the CEO of your company, asking for your assistance. The text says the CEO needs you to purchase six gift cards worth $200 apiece and send the information immediately. The sender promises repayment before the end of the day and mentions that…
Read More4 Ways To Make Data Breaches Cheaper
Businesses want to avoid data breaches at all costs, but they offer an increasingly common threat in today’s environment. In fact, 83% of organizations suffered more than one breach last year, according to the IBM Security 2022 Cost of a Data Breach Report. (IBM Security 2022 Cost of a Data Breach Report) The consequences of…
Read MoreMobile Malware Increased 500% in 2022
Cybersecurity researchers recently uncovered an alarming mobile statistic. During the first few months of 2022, mobile malware attacks surged by 500%. This spike is alarming both in scale and because many people aren’t yet protecting smartphones. For years, mobile phone evolution gave them more and more power. They now function much like a computer –…
Read More2023 Data Privacy Trends Impacts
Data privacy has been a growing requirement ever since the internet age began. So much personal information is flying around through computer networks. Protecting it has become a mandate. Most companies must follow HIPAA, GDPR, or another industry or locality-based privacy rule. By the end of 2024, 75% of the world’s population will have their…
Read MoreExposed By A Data Breach?
Browsers like Edge have added breached password notifications for a reason. Data breaches represent an unfortunate part of modern life. These breaches often mean costly consequences for individuals. Hackers steal identities and compromise bank accounts, just to name a couple of favorite targets. Cybercriminals breach approximately 4,800 websites every month with form jacking programming. It…
Read More8 Tech Checks to Make Before You Travel
Our technology always comes with us when we travel. Plenty of people won’t even travel to the end of the block without smartphone in hand. Whenever you go on a trip, missing your technology when you need it can ruin your day. Here at NoContractVoIP, we specialize in making business phone systems fully portable. No…
Read MoreCybersecurity Attack Trends In 2023
The new year is just beginning, offering a time of renewal as we all plan for the possibilities to come in 2023. Now also represents a time when companies should plan for resiliency in the face of ever-present cyberattacks. Sixty-eight percent of surveyed business leaders believe that cybersecurity risks are getting worse. They have a…
Read More